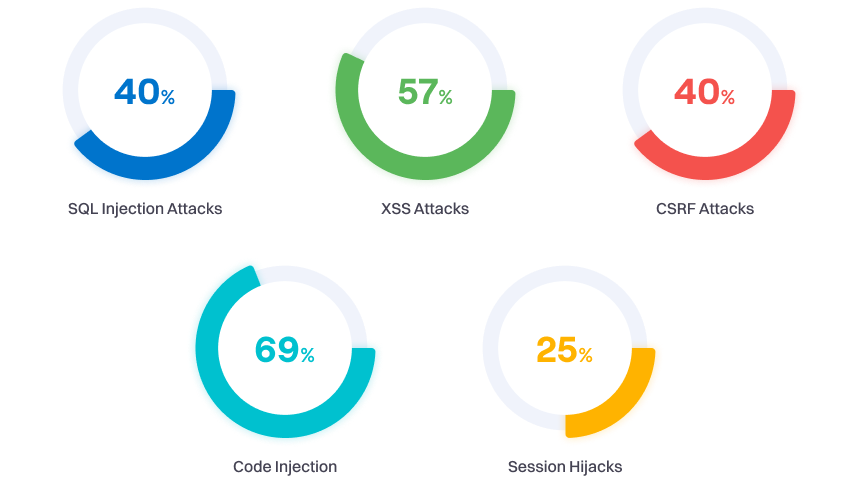
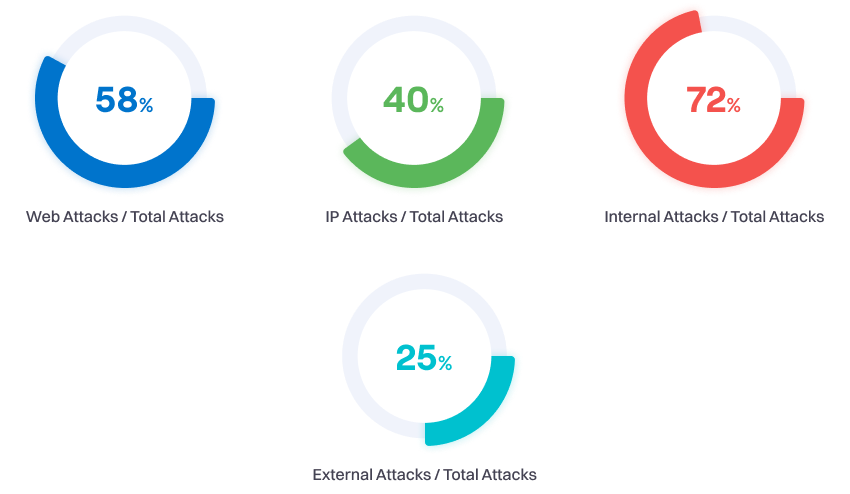
Computer Forensics

When your security has been breached, it’s not enough to
respond and recover. You need professional, fast assistance
to protect your organisation and arm you for the potential
legal battle ahead. Few companies are ready with the logs,
processes, playbooks and training it takes to control the
chaos resulting from compromised security.
Computer forensics is the collection and analysis of digital
evidence in administrative, civil and criminal cases. As a
service, computer forensics is a fast response from a
well-oiled team of experts with the tools and experience to
set you up for success in the courtroom.
Computer crime cases are complex, and they require
exceptionally skilled support specialists for legal
professionals. Mitnick Security will act as an extension of
your own team, helping you to build a solid case through
digital evidence of theft, policy violations, misuse of
computing and other assets, hacking activities, digital
harassment, embezzlement, sabotage, industrial espionage,
falsification of data and more.
Our Five-Phase Approach to Computer Forensics
The Global Ghost Team™ approaches each case methodically,
using the highest industry standards and proven scientific
methods to evaluate evidence. Our five-phase approach and
diligent persistence has saved careers, reputations and
even incarceration time for our clients.
1. Data Imaging Phase
Once your custom project team obtains an image of
potential evidence from your system, we begin by making
at least two copies, so we never work on the original
forensic data. Then, while imaging, hardware
“write-blockers” are used to ensure the evidence isn’t
corrupted. Our team also generates a hash of the
evidence images we collect, to inspect the integrity of
the images during later analysis. All of this is done to
maintain evidence integrity, to create a solid
foundation for your case.
2. Extraction Phase
In the extraction phase, the Global Ghost Team™ sets up
and validates forensic hardware and software, creating
the system configuration as needed. The integrity of the
forensic data is then checked by using the previously
generated hash before we begin extraction.
3. Identification Phase
In this phase, the Global Ghost Team™ processes
extracted data, identifying information that could be
relevant to the case and filtering everything into one
of three categories: relevant, irrelevant and outside
scope.
Data classified as “outside scope” consists of
incriminating information that lies beyond the scope of
the warrant or request. In this case, you’re immediately
notified and able to consult with the relevant
professionals before taking action.
Once all relevant data is placed identified and
organised, our team then hunts for new potential data
search leads; or sources. Now, you’re made aware of our
initial findings.
Analysis Phase
The Global Ghost Team™ analyzes the data, looking for
evidence to support or refute the case, including:
-
Who: Knowledge about the user or application that created,
edited, modified and sent, or received the file. We will
also determine who the data is linked to and identified
with.
-
When: The days and times when a data item was created,
edited, modified, sent, received, viewed, deleted and so
on.
-
Where: The location the data was found, where it
originated and where relevant events took place.
-
How: We’ll determine how data came to be on the media as
well as how was it created, modified, transmitted, etc.
-
Other Important Information: As part of a thorough process
and full picture of the incident, we’ll also inspect
registry entries and system or applications logs, analyze
metadata and determine whether there are links to another
event.
Reporting Phase
Across all of our cybersecurity services, Mitnick Security is known for delivering the gold standard in case reports. All of our findings will be turned over to your team in an easy-to-understand digital document that includes images and hyperlinks to evidence for easy navigation and comprehension.
Each report begins with an overview or Case Summary then presents the relevant information about how each image was obtained, how the analysis began and a summary of what we found. You’ll also receive details of how our team handled the evidence and the steps we took to preserve data integrity through each step.